“Phishing” is a cute name for a malicious practice. An attacker sends millions (or even a billion) of emails that tries to convince someone it’s from a legitimate source. Phishing sometimes relies on the billions of account compromises that have occurred over the last several years to include telling personal details, like your mailing address or an account name associated with a site.
The mail convinces you something is wrong with your account, or there’s a great promotion underway, and urges you to click a link that looks correct. Clicking brings you to a website that wants your account credentials. Proceed—and you may have given away the keys to your kingdom.
This kind of attack is insidious because most of us receive so much email from companies and organizations we deal with that we can barely manage all of it. A message that says “credit card exceeded limit!” may rise above the fray, and you pay attention. The site to which the email is linked looks just like what you expect.
I speak from a position of a fellow sufferer. Over the last year, I’ve received a text message from “DHL” and two emails from “American Express” that nearly got me. I clicked the DHL message, as I was expecting a package from that service, which is rare for me—and quickly realized what I was doing and closed the window. With the Amex messages, they both wound up filtered into my spam folder, but I looked at them and thought, “This must be in error.” However, on closer examination, I realized my spam app was more observant than I was, and I never clicked at all.
Here’s what you can do to resist these attacks in an email message.
Disable loading images
Invisible tracking pixels allow both marketers and scammers to know a message was opened and may reveal more than you want about yourself. You can follow these instructions to disable automatic image and media loading. Starting with the release later this year of iOS/iPadOS 15 and macOS 12 Monterey, you can go further by enabling Mail Privacy Protection, which loads trackers through a proxy to break the connection to you. (This feature doesn’t require iCloud+, the new name for paid iCloud tiers.)
Don’t click on site links in email
While it’s convenient to click links in emails, not clicking links and instead using bookmarks or typing the first few letters of a site bypasses most phishing attacks.
Hover over links before clicking
If you’re thinking of clicking and have an email client (like Apple’s Mail) that supports it, you can hover over any link and see what it looks like. If it’s not the URL of the company or group who sent it, don’t click. Some companies use email tracking and route their links through Mailchimp and other legitimate email-sending firms. But you can’t differentiate between use and misuse in those cases. With Apple email, hovering over shows the URL as tip text; only when you click the downward-pointing arrow do you get a full preview, which I recommend not doing given the risk of providing more information about yourself.
Look for warnings in email
Some email apps automatically warn you or you can enable warnings that tell you a message looks suspicious or has links to point to known phishing sites. I use Postbox, which has this option. It’s not always accurate—it dislikes eBay’s emails for some reason—but it at least makes me warier of an incoming email.
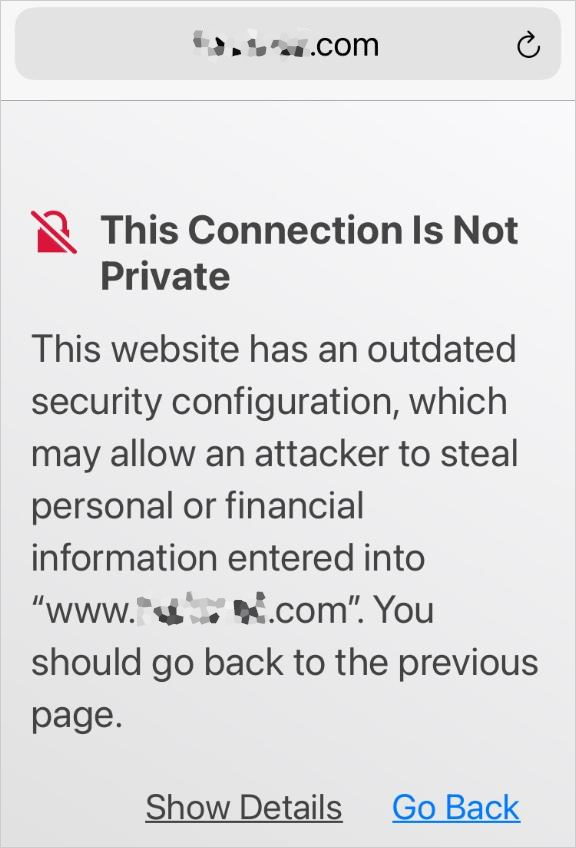 https://www.macworld.com/wp-content/uploads/2021/06/mac911-insecure-connection.jpg?resize=204%2C300&quality=50&strip=all 204w" sizes="(max-width: 576px) 100vw, 576px" />
https://www.macworld.com/wp-content/uploads/2021/06/mac911-insecure-connection.jpg?resize=204%2C300&quality=50&strip=all 204w" sizes="(max-width: 576px) 100vw, 576px" />If you decide the link is legitimate and go ahead and click it, be wary and follow this advice:
- Check the padlock. Safari and most other browsers display a lock icon in the Location or similar bar at the top of their window in desktop and mobile versions. If you don’t see a padlock, it’s a problem.
- Watch for blatant security warnings. Safari throws up a big warning when you visit a site that’s using a security document (a digital certificate) that doesn’t match the domain name it’s at. That’s a huge red flag and you should walk briskly away in a virtual sense. You have to do work to bypass this warning.
- Watch for subtler security warnings. Apple also checks in Safari for an expired security document (sites have to renew at least annually) that was formerly legitimate. And if you’re on a non-secure page that asks for your password or credit card. Those are red flags as well.
- Use a password manager. Apple’s built-in password support across iOS, iPadOS, and macOS and 1Password and other third-party ecosystems will only fill in a password if the domain matches precisely. A look-alike domain meant to fool you will never match, and thus you won’t be offered the opportunity to click or use Touch ID or Face ID to fill in the login fields.
The one occasion in which you will see an error when you’re trying to visit the legitimate version of a site is when you’re at a public hotspot and haven’t yet jumped through their hoop to join the network. When you connect to such a hotspot, it blocks general Internet traffic. It effectively redirects everything to a local “portal” page where you can pay, enter a login, or agree to terms of service for free access.
Until you pass the portal page, any other web page you visit will produce an error that looks like you’re at a fraudulent site.
This Mac 911 article is in response to a question submitted by Macworld reader Tom.
Ask Mac 911
We’ve compiled a list of the questions we get asked most frequently, along with answers and links to columns: read our super FAQ to see if your question is covered. If not, we’re always looking for new problems to solve! Email yours to mac911@macworld.com, including screen captures as appropriate and whether you want your full name used. Not every question will be answered, we don’t reply to email, and we cannot provide direct troubleshooting advice.