In early December 2022, Apple announced a significant change to iCloud data encryption. Previously, Apple split the way it protected your data synced via iCloud:
- Some of your data (photos and other media, reminders, and notes) relied on encryption keys held by Apple to protect your data when at rest–that is, while stored on its servers. You could access all of this via iCloud.com by logging in. When Apple syncs this data, it relies on encrypted HTTPS and similar secured connections between your devices and apps and its servers.
- Other parts of your data, an increasing amount over the year, relied on end-to-end encryption (E2EE), in which the keys for encrypting and decrypting your data are only stored on your devices and only accessible by your action on those devices. Apple has no access to the keys at all. Those kinds of data include Health information, Safari bookmarks, and iCloud Keychain. None of this data could be accessed at iCloud.com; iCloud was just a conduit for syncing among devices. (Apple also encrypts this data in transit, but that’s a layer on top of E2EE, not instead of E2EE.)
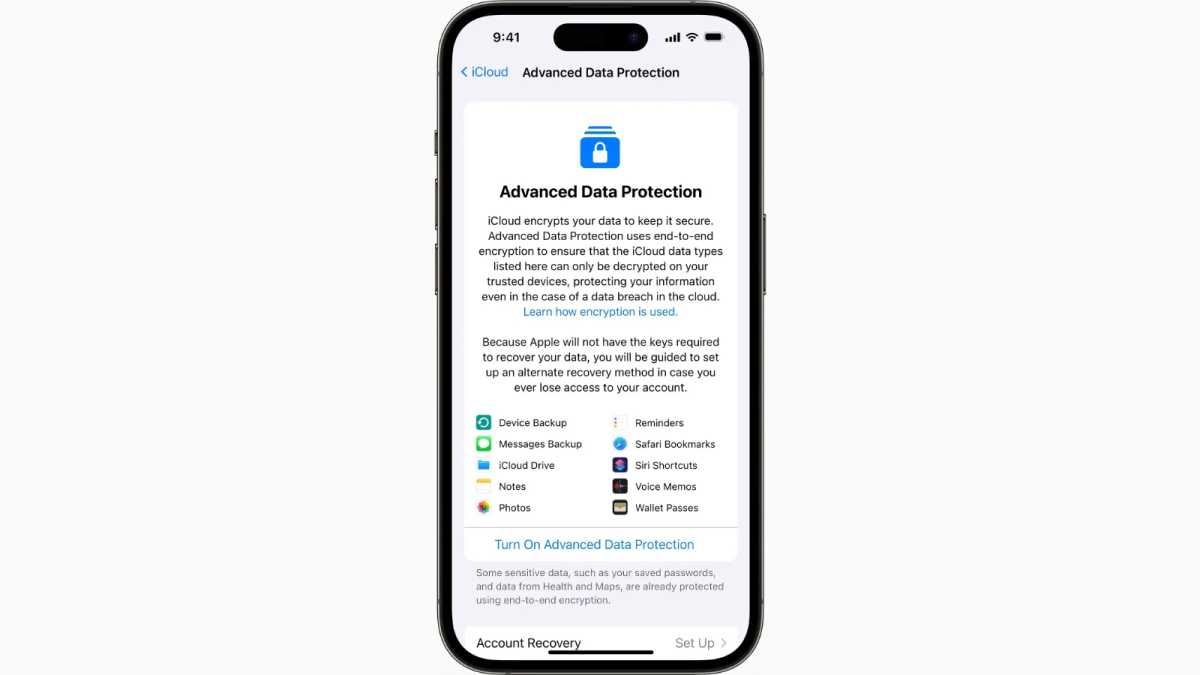
On Dec. 13, 2022, Apple rolled out Advanced Data Protection, an option that lets you shift nearly all your Apple-secured data at iCloud to E2EE. Instead of Apple holding the keys for data at rest on its servers, that data would be effectively impossible to retrieve for anyone who lacked one of your devices, like an iPhone or Mac, and the ability to unlock that device.
Apple had to exempt email, contacts, and calendar entries from this shift, however. Those three categories of items are always protected at rest with Apple-controlled encryption. But for compatibility with third-party email, contact, and calendar apps and online services, there’s no current way to allow end-to-end encryption while still making the underlying data accessible. (That could change in the future, but it requires a huge industry shift that has shown only glimmers of happening. Google has just rolled out a beta of end-to-end encrypted email.)
You don’t have to enable ADP if you don’t want to. ADP has drawbacks in terms of management, access, and recovery. As with other E2EE methods, you are at risk of losing access to your data forever if you lose or are locked out of all your devices and other recovery methods fail to work. Apple requires that you enable some recovery features to avoid this, discussed below, but it remains a risk.
 https://b2c-contenthub.com/wp-content/uploads/2022/12/icloud-advanced-data-protection.jpg?resize=300%2C168&quality=50&strip=all 300w, https://b2c-contenthub.com/wp-content/uploads/2022/12/icloud-advanced-data-protection.jpg?resize=768%2C432&quality=50&strip=all 768w, https://b2c-contenthub.com/wp-content/uploads/2022/12/icloud-advanced-data-protection.jpg?resize=1200%2C675&quality=50&strip=all 1200w, https://b2c-contenthub.com/wp-content/uploads/2022/12/icloud-advanced-data-protection.jpg?resize=1536%2C864&quality=50&strip=all 1536w, https://b2c-contenthub.com/wp-content/uploads/2022/12/icloud-advanced-data-protection.jpg?resize=1240%2C697&quality=50&strip=all 1240w, https://b2c-contenthub.com/wp-content/uploads/2022/12/icloud-advanced-data-protection.jpg?resize=150%2C84&quality=50&strip=all 150w" width="1200" height="675" sizes="(max-width: 1200px) 100vw, 1200px" />
https://b2c-contenthub.com/wp-content/uploads/2022/12/icloud-advanced-data-protection.jpg?resize=300%2C168&quality=50&strip=all 300w, https://b2c-contenthub.com/wp-content/uploads/2022/12/icloud-advanced-data-protection.jpg?resize=768%2C432&quality=50&strip=all 768w, https://b2c-contenthub.com/wp-content/uploads/2022/12/icloud-advanced-data-protection.jpg?resize=1200%2C675&quality=50&strip=all 1200w, https://b2c-contenthub.com/wp-content/uploads/2022/12/icloud-advanced-data-protection.jpg?resize=1536%2C864&quality=50&strip=all 1536w, https://b2c-contenthub.com/wp-content/uploads/2022/12/icloud-advanced-data-protection.jpg?resize=1240%2C697&quality=50&strip=all 1240w, https://b2c-contenthub.com/wp-content/uploads/2022/12/icloud-advanced-data-protection.jpg?resize=150%2C84&quality=50&strip=all 150w" width="1200" height="675" sizes="(max-width: 1200px) 100vw, 1200px" />Apple
The advantage of ADP is that nearly all your data is inaccessible in the event of a breach of Apple’s servers, a hack of your security, legitimate or illegitimate government demands, or criminal efforts. Without possessing an unlocked device linked to your account, you’re protected against disclosure of covered types of information.
So far, only customers in the U.S. can turn on ADP. Apple promises to give access to customers in more countries in 2023, including China.
What sort of data is covered by Advanced Data Protection?
Apple has a rundown on a support webpage of the different methods of encryption it uses for each offered service or data storage type, including whether or not the ADP is enabled. Here’s how it works, with standard and ADP encryption called out for each point.
- Always encrypted at rest (standard and ADP): Email messages, calendar events, and contacts. These cannot be encrypted using E2EE, as noted above.
- Either encrypted at rest (standard) or E2EE (ADP): iCloud backups, Find My (Devices and People), iCloud Drive, your iCloud for Message’s encryption key (see below), Notes, Photos, Reminders, Siri Shortcuts, Voice Memos, and Wallet passes plus iWork apps (Keynote, Numbers, and Pages). Find My (Devices only), iCloud Drive, Notes, Photos, Reminders, and iWork files can also all be accessed via iCloud.com with ADP on or off—although see below for a new option to control this.
- Always encrypted at rest (ADP): Metadata associated with the above services, such as thte name and serial number of a device associated with an iCloud Backup, the number of views of an image or video in iCloud Photos, and the last modification date of a Safari bookmark. (Apple has a full list of metadata exceptions near the bottom of this page.)
- Uses E2EE while shared (ADP): With ADP active, E2EE remains active for most data you share with other people if they have ADP enabled. If they don’t, notes, reminders, iCloud Drive folders and files, and some other items are only encrypted at rest.
- Doesn’t use E2EE while shared (ADP): Apple lists a number of other exceptions to E2EE for shared items: Keynote, Numbers, and Pages files shared via iCloud collaboration; Shared Albums in Photos; and anything shared using for content that Apple offers the “anyone with the link” action.
- Always uses E2EE (standard and ADP): Apple Card transactions, your iCloud for Messages message contents (see below), Home data, Health data, iCloud Keychain, Find My items’ location (like AirTags), Maps details (like your search history and places marked as favorites), Memoji, payment information, QuickType Keyboard learned vocabulary, Safari (bookmarks, history, and iCloud Tabs), Screen Time settings and data, Siri information, Wi-Fi passwords, and Bluetooth keys used with Apple’s W1 and H1 chips. While this information is synced over iCloud, it can’t be accessed via iCloud.com.
Messages in iCloud is a quirky exception. Without ADP enabled, Apple encrypts the contents of your messages as stored in iCloud using E2EE. But if you have iCloud backups also turned on, the decryption key for your messages is stored in the backup, and the backup is only encrypted under the control of Apple. This makes it susceptible to cracking. If you enable ADP, both the contents of your messages and the encryption key to descramble them are protected because E2EE protects your iCloud backups.
I can summarize the ADP and non-ADP versions of iCloud encryption in a different way:
- With ADP enabled, what’s E2EE: Everything you store in iCloud uses E2EE except email, contacts, and calendar events, certain kinds of metadata, and certain items when shared, as noted above.
- With ADP disabled, what’s E2EE: Only the items listed in the last bullet point above plus the Messages in iCloud exception in iCloud Backups.
Starting also in iOS 16.2, iPadOS 16.2, and macOS 13.1, you can choose to disable access to data otherwise available when you log into iCloud.com, whether or not you have ADP enabled. Go to Settings (iOS/iPadOS)/System Settings (macOS) > Account Name > iCloud and disable Access iCloud Data on the Web.
 https://b2c-contenthub.com/wp-content/uploads/2022/12/adp-devices-out-of-date-bordered.png?resize=185%2C300&quality=50&strip=all 185w, https://b2c-contenthub.com/wp-content/uploads/2022/12/adp-devices-out-of-date-bordered.png?resize=768%2C1247&quality=50&strip=all 768w, https://b2c-contenthub.com/wp-content/uploads/2022/12/adp-devices-out-of-date-bordered.png?resize=739%2C1200&quality=50&strip=all 739w, https://b2c-contenthub.com/wp-content/uploads/2022/12/adp-devices-out-of-date-bordered.png?resize=946%2C1536&quality=50&strip=all 946w" height="1200" sizes="(max-width: 739px) 100vw, 739px" />
https://b2c-contenthub.com/wp-content/uploads/2022/12/adp-devices-out-of-date-bordered.png?resize=185%2C300&quality=50&strip=all 185w, https://b2c-contenthub.com/wp-content/uploads/2022/12/adp-devices-out-of-date-bordered.png?resize=768%2C1247&quality=50&strip=all 768w, https://b2c-contenthub.com/wp-content/uploads/2022/12/adp-devices-out-of-date-bordered.png?resize=739%2C1200&quality=50&strip=all 739w, https://b2c-contenthub.com/wp-content/uploads/2022/12/adp-devices-out-of-date-bordered.png?resize=946%2C1536&quality=50&strip=all 946w" height="1200" sizes="(max-width: 739px) 100vw, 739px" />If you enable iCloud data access when it’s turned off and you have ADP enabled, Apple prompts you with an additional warning that explains you have to use a trusted device every time you want to gain access. Tap or click Access iCloud Data on the Web to proceed and then tap or click Allow Access.
If you’re ready to set up ADP, start with the prerequisites and preparation required to ensure you don’t lock yourself permanently out of your own data.
Check Advanced Data Protection Requirements
To use ADP, all of your hardware must be using a minimum release of its respective operating system: iOS 16.2, iPadOS 16.2, macOS 13.1 Ventura, tvOS 16.2, watchOS 9.2, and HomePod 16.2. Yes, an out-of-date HomePod or HomePod mini needs its refresh before you proceed to enhance your iCloud security.
Your iCloud account has to have two-factor authentication enabled, which is almost always the case these days. Apple force upgraded most of us years ago. But if you haven’t upgraded yet, consult this article. All your devices must have passcodes, too, but I would be shocked if you’re reading this book and that isn’t the case.
You also need to reside in the United States to use ADP as of its rollout in December 2022. Apple promises more countries in 2023 without a timetable or a list.
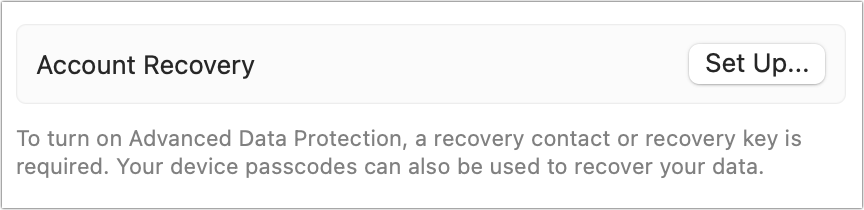
Finally, you have to turn on a form of account recovery to help if you lose access to your iCloud account login. Apple notes you can use a recovery contact or a recovery key. I suggest setting up both to give yourself even more protection. For details on both of those, see “How to use iCloud Data Recovery Service” and “What you should know about iOS 15 recovery keys.”
Apple also lets you know that you can recover data if you have the passcode for the device you use to enable ADP. That’s because E2EE keys for ADP are additionally wrapped with device passcode protection. With a device passcode, you can unlock the keys necessary to access device-based encrypted data. Because your passkey isn’t stored in an accessible way, this doesn’t reduce the security of your device or your iCloud data.
Enable Advanced Data Protection
Start by going to the ADP setting section: Settings (iOS/iPadOS)/System Settings (macOS) > Account Name > iCloud > Advanced Data Protection. Tap Turn On Advanced Data Protection or click Turn On.
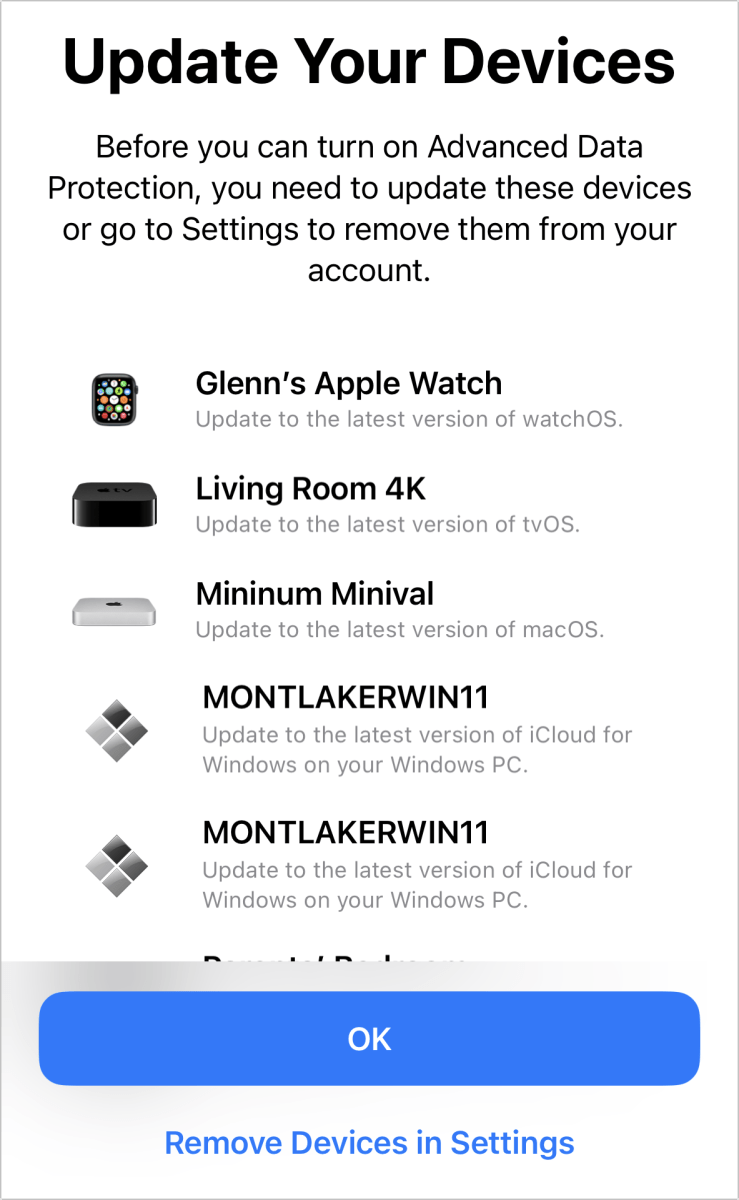
If all your devices aren’t up to date, you’re told which ones require a newer version of their OS. You can opt to either complete upgrades or remove devices with older operating systems from your account by tapping Remove Devices in Settings.
 https://b2c-contenthub.com/wp-content/uploads/2022/12/adp-recovery-required-bordered.png?resize=300%2C73&quality=50&strip=all 300w, https://b2c-contenthub.com/wp-content/uploads/2022/12/adp-recovery-required-bordered.png?resize=768%2C187&quality=50&strip=all 768w" width="864" height="210" sizes="(max-width: 864px) 100vw, 864px" />
https://b2c-contenthub.com/wp-content/uploads/2022/12/adp-recovery-required-bordered.png?resize=300%2C73&quality=50&strip=all 300w, https://b2c-contenthub.com/wp-content/uploads/2022/12/adp-recovery-required-bordered.png?resize=768%2C187&quality=50&strip=all 768w" width="864" height="210" sizes="(max-width: 864px) 100vw, 864px" />Once you’re up to date, you can proceed. If you have at least one account recovery option enabled, Apple now lets you turn on ADP:
- Apple warns you that “you will be responsible for your data recovery.” You have to tap or click the Review Recovery Methods options.
- If you have a Recovery Key enabled, you must enter it and tap or click Next.
- With the Recovery Key accepted, enter your device passcode when prompted.
- Finally, you’re told “Advanced data Protection is On.” Tap or click Done. You should also receive an email message at your iCloud.com address that tells you ADP was enabled.
Access Advanced Data Protection-protected Data via iCloud
 https://b2c-contenthub.com/wp-content/uploads/2022/12/adp-icloud-banner-bordered.png?resize=300%2C231&quality=50&strip=all 300w" width="752" height="579" sizes="(max-width: 752px) 100vw, 752px" />
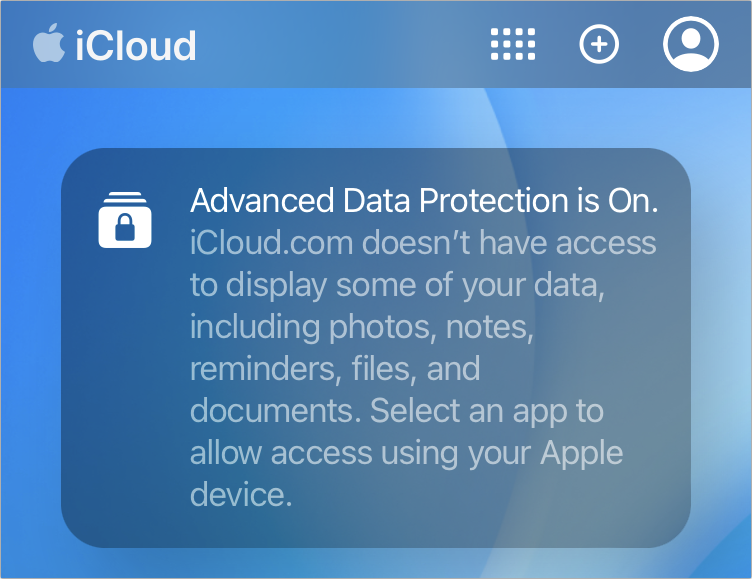
https://b2c-contenthub.com/wp-content/uploads/2022/12/adp-icloud-banner-bordered.png?resize=300%2C231&quality=50&strip=all 300w" width="752" height="579" sizes="(max-width: 752px) 100vw, 752px" />With ADP enabled, all your data except email, contacts, and calendar entries are encrypted by keys held on your devices. That would appear to count iCloud.com access out. But Apple has a workaround. They allow temporary access using in-browser encryption.
Here’s how to unlock temporary access:
- Visit icloud.com in a browser and log in.
- Apple shows a banner that explains that ADP is on and how to proceed.
- Select an app, such as Photos.
- Apple sends an access request to trusted devices.
- On a trusted device, tap or click Allow Access (Figure 100).
- On your trusted devices, a banner appears alerting you that you’ve enabled temporary access.
Data remains accessible for an hour from each request. Each additional data type you want to access may require another permission request and approval unless you request it shortly after a previous request.
Disable Advanced Data Protection
Disabling ADP is straightforward. Go to Settings (iOS/iPadOS)/System Settings (macOS) > Account Name > iCloud > Advanced Data Protection. Tap Turn Off Advanced Data Protection or click Turn Off. Follow the prompts to agree that you understand you’re removing E2EE protection from many kinds of your synced and stored data.